Disable Json API, Login Lockdown, XMLRPC, Pingback, Stop User Enumeration Anti Hacker Scan Plugin
Firewall, Scanner, block user enumeration & TOR, disable Json API, xmlrpc & Pingback, Hide Version, Login error message, Notifications, more...
ANTI HACKER PLUGIN
★★★★★
No matter how small or big your server is, hackers may attempt to use it to send spam, steal traffic, and attack other computers. According to Security magazine, there is a hacker attack every 39 seconds.
In fact, some studies suggest that the majority of attacks against websites begin to occur within the first 24 hours of a site going online.
.
Improve system security, protect login (Login Security), firewall, scan for malware, block user enumeration and TOR, disable Json WordPress Rest API, xmlrpc (xml-rpc) & Pingback and more a lot of security tools. Multilanguage ready. Included also Italian and Portuguese language files.
.
Italian: Migliora la sicurezza del sistema, proteggi l’accesso (sicurezza dell’accesso), firewall, cerca malware, blocca l’enumerazione degli utenti e TOR, disabilita l’API Rest di Json WordPress, xmlrpc (xml-rpc) e Pingback e molti altri strumenti di sicurezza. Multilingua pronto. Inclusi anche file in lingua italiana e portoghese.
.
Português: Melhora a segurança do sistema, proteje o login (Segurança de login), firewall, verifica se há malware, bloqueia a enumeração do usuário e TOR, desativa Json WordPress Rest API, xmlrpc (xml-rpc) e Pingback e mais muitas ferramentas de segurança. Pronto para vários idiomas. Incluídos também arquivos em italiano e português.
- No DNS API (entryPoint) or Cloud Traffic Redirection. No Slow Down Your Site! No Google penalties for slow sites.
Features and Tools Included
- Prevent unauthorized access to your account by protect your login page also against bots and brute force.
- Firewall to Block Malicious Requests, Queries, User Agents and URLS. 100% Plug-n-play, no configuration required.
- View Table of the Blocked Visits and add IP to Whitelist from table and logs failed login attempts.
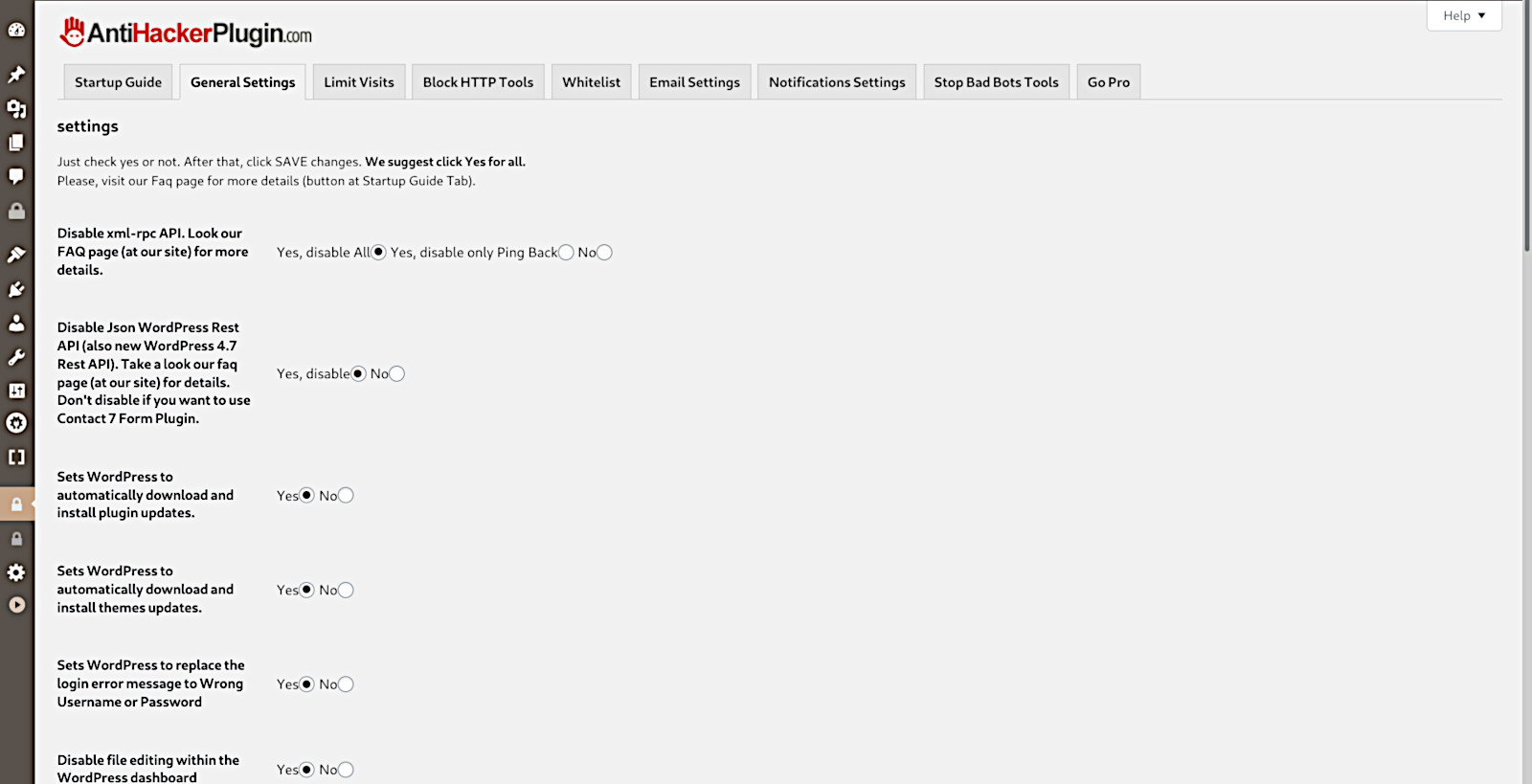
- Option to disable Json WordPress Rest API (also new WordPress 4.7 Rest API).
- You can also disable the WordPress xmlrpc (xml-rpc) (or disable only Pingback) API with just one click.
- You can turn on login alerts with just one click. Also login fails alert.
- Send alert email when any new plugin is installed. (First thing hackers do when gain access to your site)
- Send email alert when AntiHacker plugin in deactivated.
- WordPress Debug enabled warning.
- Disable file editing within the WordPress dashboard.
- Replace insecure login error message.
- Hide WordPress version number.
- Disable Application Passwords: Block external applications to request permission to connect to a site and generate a password (WordPress 5.6 new feature)
- Limit Visits, Limit Bots Attempts (Premium Version)
- limit only 404 requests (Premium Version)
- Check Google Safe Browsing Blacklist
- Check and alert for deactivated Plugins and themes
- Check and alert for extra files and dangerous files on root folder.
- Multilingual ready.
- Disable WordPress native sitemap (for user’s) creation.
- Disable xmlrpc
- Disable Pingback
- Protect Against Cyber Attack
- hardening wordpress
Malware Scanner
- Security Malware scanner (one click scan) for 797 malwares also in free version (unlimited files).
- 7 speed options to scan and the scan run on your local computer to not overload your server.
- Scans every folder and inspects every file on a website (deep scanner) for traces of malware, exploits, trojans, worms, viruses, backdoors as well as JavaScript code obfuscation, exploits, malicious iframes, malicious code injection, malicious code obfuscation, auto-generated malicious content, redirects, hidden eval code and more.
- Scan all Pages, Posts and Comments against malwares.
- Alert for plugins and themes without updates for long time or with old versions.
- Scan your site now before Google blacklists it or your web host takes it down.
Block
- User enumeration. (is one of the most popular attacks to identify the valid user names)
- Comments in media page.
- Bad Queries.* Block All Feeds (Optional).
- Creation of new Administrators from plugins and themes with vulnerabilities.
- False Google and Bing (MSN) bots (Premium Version)
- Search for Theme’s vulnerabilities (Premium Version)
- Search for Plugin’s vulnerabilities (Premium Version)
- Tor (The Onion Router) Traffic – Optional – (Premium Version) Tor anonymity provides value to online attackers.
- HTTP Tools (you can manage the strings)
- Blank User Agent
Useful Links
Demo Video
Premium Version with more features
(Our Premium version won’t empty your pocket.)
StartUp Guide
Online Documentation
FAQ Page
Plugin Site
Plugin Blog with a lot of tips
Compatible with Stop Bad Bots Plugin
Share 🙂
Why disable the WordPress xmlrpc
This plugin disables XMLRPC API in WordPress 3.5+ or above, which is enabled by default.
XMLRPC on WordPress is actually an API or “application program interface“.
It gives developers who make mobile apps, desktop apps and other services the ability to talk to your WordPress site.
Most users don’t need WordPress XMLRPC functionality, and it’s one of the most common causes for exploits.
If you want to access and publish to your blog remotely, then you need XMLRPC enabled.
Why should we disable pingbacks?
Pingback allows you to notify other bloggers that you have linked to their article on your website.
A WordPress website with Pingback enabled can be used in DDOS attacks against other websites.
An attacker can exploit pingback functionality through simple command and an XMLRPC request.
Why disable Json WordPress Rest API
(disable WordPress Rest API)
Block User enumeration to improve security.
The REST API (new WordPress 4.7) allows for anonymous access and this means that anyone can list all
the users of a website. This will enable botnets to try and Bruteforce attack a website with the user’s credentials.
Brute Force Login Protection
A brute-force attack is an attempt to discover a password by systematically trying every
possible combination of letters, numbers, and symbols until you discover the one correct combination
that works.
Our plugin will protect your site against Brute Force Attack, by restrict access to login page to
whitelisted IP addresses.
Otherwise, your login page will request your wordpress user email.
It is not necessary Limit Login Attempts. Read below about Rate Limiting.
Rate Limiting
Rate Limiting is a substitute to Limit Login Attempts.
Bots and Hackers can make a lot of visits in a short time period.
We can just limit a number of visits.
Simple Login Lockdown
Rate Limiting is a substitute to Simple Login Lockdown. Read above.
Rename wp-login.php
Rate Limiting is a substitute to Rename wp-login.php. Read above.
External service
If the settings of Anti Hacker is Block all traffic from Tor? = “Yes”, we can test visitors Ip
from the TOR PROJECT database. We download daily Tor Database and we didn’t send any information to them.
This is a free service. TorProject is a not-for-profit organization.
Tor Documentation:
https://www.torproject.org/
External service 2
Our plugin will check your status on Google regarding Google Safe Browsing.
Google Safe Browsing is a service provided by Google to help protect users from malicious websites on the internet.
To simplify your inquiry, avoiding the need to create a Google account to obtain an API,
we will perform this query for you.
We will send your domain address and Google will inform us whether it considers your site safe or not.
Obviously, if it does not consider it safe, it will not send visitors to your site.
Instead, it will inform those who intend to visit your site that it is dangerous.
Hence the importance of always monitoring this. We will add that on your plugin dashboard.
This collected data (domain name) will only be used to query Google and will not be stored.
For more information about this, visit Google.
For more details about our site, visit us.
These are the terms of use for our plugins.
This plugin is a service. If you choose the premium version, only in this case, when applying your purchase code, it will be sent to our server, which will return whether it is valid or not.
Look the file changelog.txt for details
We can keep the size of the standard WordPress readme.txt file reasonable
Installation
1) Install via wordpress.org
2) Activate the plugin through the ‘Plugins’ menu in WordPress
or
Extract the zip file and just drop the contents in the wp-content/plugins/ directory of your WordPress installation and then activate the Plugin from Plugins page.
Screenshots
FAQ
- Install via WordPress.org:
- Search for the plugin within your WordPress admin panel under “Plugins” -> “Add New.”
- Click the “Install Now” button.
- Activate the plugin through the ‘Plugins’ menu in WordPress.
- Manual Installation:
- Download the zip file.
- Extract the contents.
- Upload the extracted folder to the ‘wp-content/plugins/’ directory of your WordPress installation.
- Activate the plugin from the “Plugins” page in your WordPress admin panel.
The file “ruler.txt” is a security-related file that contains signatures or patterns used to identify and detect malware. It includes nearly 900 malware signatures, which are used to compare files and data against known patterns of malicious code in order to identify potential threats.
The presence of such a file is a standard practice in security software, and it should not be a cause for concern. It indicates that your antivirus or security tool is actively scanning and protecting your system against known malware threats.
You can find the Online Manual at http://antihackerplugin.com/?p=20.
The Online FAQ page is available at http://antihackerplugin.com/faq/.
For support, please visit http://billminozzi.com/support/.
You can find more free tips on our blog at https://antihackerplugin.com/blog/.
Our WordPress anti-hacker plugin significantly boosts your site’s security by disabling WordPress XML-RPC
feature. WordPress XML-RPC is a protocol that allows remote access to your WordPress site,
but it has been known to be susceptible to various XML-RPC exploits and XML-RPC attacks.
Disabling XML-RPC with our plugin prevents potential XML-RPC attacks and XML-RPC exploits,
ensuring that your site remains secure from unauthorized access and other security threats.
By using our plugin to disable XML-RPC in WordPress, you can protect your site from these vulnerabilities
without compromising functionality.
To prevent unauthorized login attempts and receive timely notifications, I recommend using the “AntiHacker” plugin. This plugin addresses the issue by adding an email field to the login page, ensuring that only whitelisted users can log in. When an unauthorized login attempt occurs, the plugin triggers a login error message, informing the user that their access is denied. Additionally, AntiHacker offers robust security features, including login lockdown to prevent multiple failed attempts, and comprehensive login alerts. You will receive admin login notifications and login notifiers to keep you updated on any suspicious activity. With AntiHacker, you can stay informed through login notifications and maintain control over your site’s security.